Hi Kim thanks for your response its appreciated. When a domain controller.

Solved Eventid 4776 Help Me Identify The Source Of A Brute Force Rdp Attack It Security
They are logging on with local accounts to Windows 7 Enterprise desktops which are not part of the domain.
. Through the 4776 event log we can obtain the source workstation address log in to the computer and refer to the below steps to check. They connect to network shares. Active-directory windows-server-2008-r2 authentication windows-event-log wireshark.
This event is also logged on member servers and workstations when someone attempts to logon with a local account. Tengo Windows 7 Profesional 64 bit unido a un dominio resulta que desde ha ce 15 dias se me bloquea un usuarios el mio logro ingresar al sistema pero cuando voy a ver mis unidades de red me sale que estoy bloqueado. This usually occurs in batch-type configurations such as scheduled tasks or when using the RUNAS command Do you have any of those.
Same is used for accessing ms sql server database. Il sagit toujours de MICROSOFT_AUTHENTICATION_PACKAGE_V1_0 pour lévénement 4776. The problem is that no IP address is being logged in the security event log.
There should be only one event. Hello hope someone can help users are getting intermittently locked out by domain controllers which are Windows 2008 R2 hosted in VMWare VSphere 50. 1This event generates every time that a credential validation occurs using NTLM authenticationThis event occurs only on the computer that is authoritative for the provided credentials.
It was a Polycom that had been off the network for months and someone must have plugged it back in recently. Did you read the last sentence. Always MICROSOFT_AUTHENTICATION_PACKAGE_V1_0 Logon Account.
CISCO ISE and MS ad event id 4776 troubleshooting Good day dears This case was asked from vendors support teams twice with no adequate outcomes no ms or ise related issue. At that point I enabled in Local Security PolicyLocal PoliciesSecurity Options. When a domain controller successfully authenticates a user via NTLM instead of Kerberos the DC logs this event.
I would look at wireshark output based on the posting below. 6 comments for event id 4776 from source Microsoft-Windows-Security-Auditing. Windows 7 account lock outs Event ID.
MICROSOFT_AUTHENTICATION_pACKAGE_V1_0 I had a similar issue with a user. Hello Thanks for your post. Name of the account Source Workstation.
Of course no workstation listed. The avmgr is domain account. Audit Incoming NTLM in this domain.
The computer attempted to validate the credentials for an account. On the Domain Controller that was repeatedly locking the account out in the Event Veiwer Security the account was locking out every 2 to 3 minutes. When I am looking at the security tab of my event viewer on a Windows Server 2008 R2 I am showing a ton of Audit Failures with Event ID 4776.
This specifies which user account who logged on Account Name as well as the client computers name from which the user initiated the logon in the Workstation field. What is causing this event and possible solution. Show activity on this post.
For every single authentication from ISE against Active Directory we see two events on DC one for audit success ID4776 and one for audit failure ID. This thread is archived. Event ID 4776 is logged whenever a domain controller DC attempts to validate the credentials of an account using NTLM over Kerberos.
Authentication Success - Event ID 4776 S. They all are event ID 4776 - Audit Failure. For local accounts the local computer is authoritative.
The administrator account is set to NOT lockout. 872013 41706 AM Event ID. When I login to client PC using local account instead of domain account several event logs are getting logged onto DC as shown below.
Remarque Le package dauthentification est une DLL qui encapsule la logique dauthentification utilisée pour déterminer sil faut autoriser un utilisateur à se connecter. Hola Puedes verificar si tu usuario quedo. Computer name where logon attempt.
Different subnets for guestpublic wifi VPN and locations within the building Heres an example from the security event log on one of the DCs yesterday. I perform an investigation of the following event from domain controller data has been obfuscated. So something is using the wrong password.
With that information we might have an inkling at the vector ie. I have a 2008 R2 DC with Windows 7 client. Event id 4776 - The computer attempted to validate the credentials for an accountEvent id 4776 - The computer attempted to validate the credentials for an account.
Integration between ISE and Microsoft Active Directory. The computer attempted. The last hope is for community.
How can I tell where these are originating and shut it down. Audit failure 4776 blank workstation. Event log search for Audit Failure on Exchange for the exact same time showed its IP in the Network information of the Event.
For Kerberos authentication see event 4768 4769 and 4771. Hola Amigos espero me puedan ayudar. For domain accounts the domain controller is authoritative.
Check the credential management to see if there are cached users old credentials Check if you have used the. This can give wrong impression that ISE is sending two authN requests when only 1 is being sent. He verificado en el active.
New comments cannot be. This event is also logged for logon attempts to the local SAM account in workstations and Windows servers as NTLM is the default authentication mechanism for local logon.
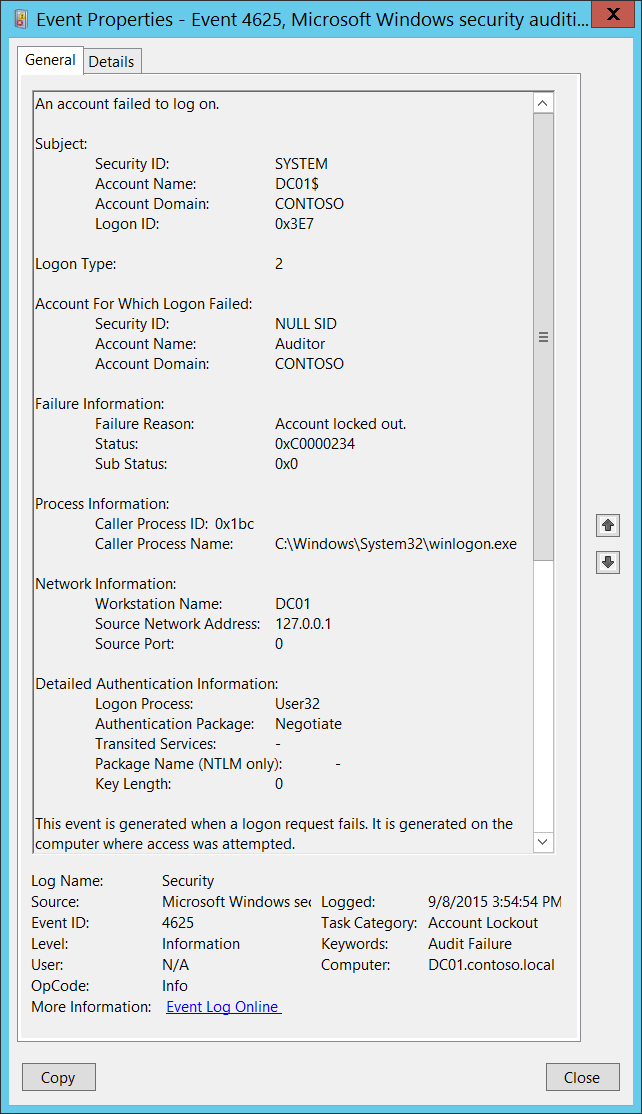
4625 F An Account Failed To Log On Windows 10 Windows Security Microsoft Docs
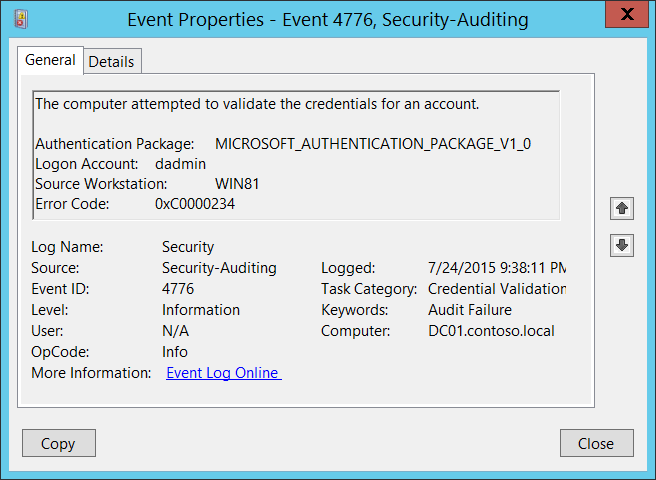
4776 S F The Computer Attempted To Validate The Credentials For An Account Windows 10 Windows Security Microsoft Docs
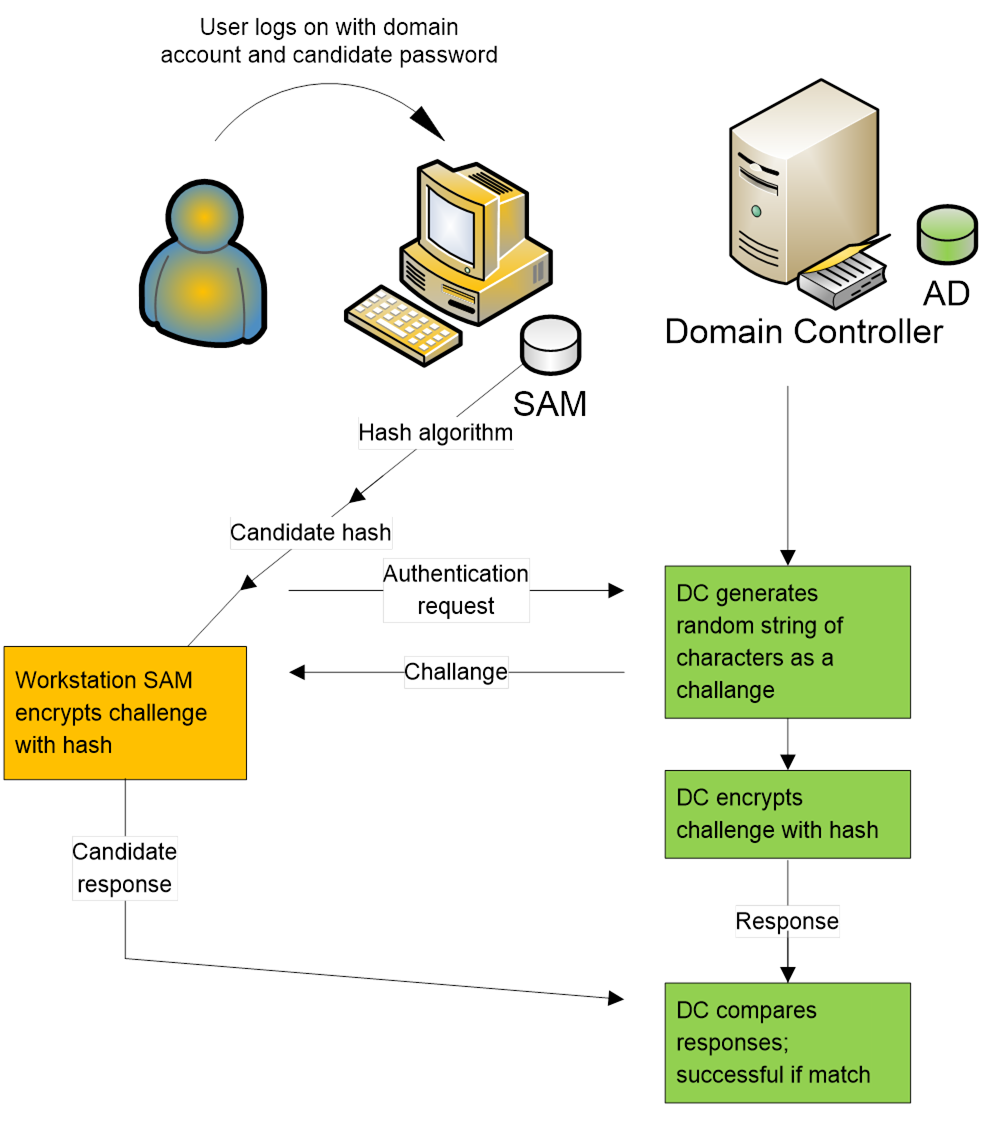
Chapter 4 Account Logon Events

Solved Eventid 4776 Help Me Identify The Source Of A Brute Force Rdp Attack It Security
Unable To Find The Source Of Account Lockout

Solved Remote Desktop Logon Failed Audit Events Windows Server
0 Comments